 题目内容
(请给出正确答案)
题目内容
(请给出正确答案)
根据所给图表、文字资料回答101~105题。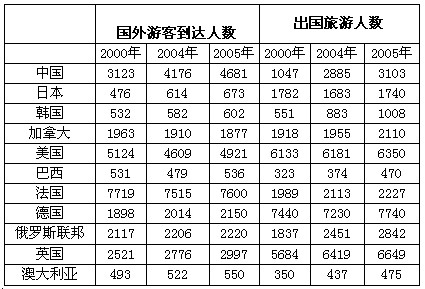 表中2005年国外游客到达人数高于出国旅游人数的国家有()。
表中2005年国外游客到达人数高于出国旅游人数的国家有()。
A.2个
B.3个
C.4个
D.5个
 如搜索结果不匹配,请 联系老师 获取答案
如搜索结果不匹配,请 联系老师 获取答案
 题目内容
(请给出正确答案)
题目内容
(请给出正确答案)
 表中2005年国外游客到达人数高于出国旅游人数的国家有()。
表中2005年国外游客到达人数高于出国旅游人数的国家有()。
A.2个
B.3个
C.4个
D.5个
 如搜索结果不匹配,请 联系老师 获取答案
如搜索结果不匹配,请 联系老师 获取答案
 更多“根据所给图表、文字资料回答101~105题。 表中2005年…”相关的问题
更多“根据所给图表、文字资料回答101~105题。 表中2005年…”相关的问题
第1题
A. MD5 authentication is supported by the Junos OS
B. Server mode is not supported by the Junos OS
C. The Junos OS can provide a primary time reference
D. The Junos OS does not support the use of a boot server
第2题
A. The Junos OS supports client, server, and symmetric modes of NTP operation.
B. Synchronized time on all network devices makes log messages more useful for troubleshooting.
C. Authentication methods are not supported.
D. The Junos OS must be used as the primary time reference.
第3题
A.Switches take less time to process frames than hubs take.
B.Switches do not forward broadcasts.
C.Hubs can filter frames.
D.Using hubs can increase the amount of bandwidth available to hosts.
E.Switches increase the number of collision domains in the network.
第4题
Which of the following is false regarding a network and a distributed system?
A.They both need to move files around.
B.They have little in common.
C.They overlap each other a lot.
D.They have different operating systems.
第5题
A.MD5 authentication is supported.
B.A client always synchronizes to a server even when the difference between the server clock and the local clock differs by a large amount.
C.JUNOS software can provide a primary time reference.
D.The boot-server configuration allows a router to synchronize its clock when it boots up, regardless of the offset between the NTP clock source and its internal clock.
E.It is useful to correlate timestamps on log files and other events for troubleshooting and forensics.
第6题
A. Once saved, a rescue configuration is loaded using the rollback 0 command.
B. The rescue configuration must contain the minimal elements necessary to restore network connectivity.
C. A minimal rescue configuration is defined by default.
D. A rescue configuration must include a root password.
第7题
Which of the statements regarding benefit-cost analysis in the Special window are true?
A . 1 and 2
B . 2 and 3
C . 1 and 3
D . 1, 2 and 3
E . None of the above.
第8题
Which of the following statements is TRUE about Robert Browning?
A.He believes that longer life is no good thing.
B.He believes that true life lies in how one makes of it.
C.He is identical with Lewis Thomas, regarding the life issue.
D.He is opposite to A.E. Housman, regarding the death issue.
第9题
A. It corresponds to a Class A address with 13 bits borrowed.
B. It corresponds to a Class B address with 4 bits borrowed.
C. The network address of the last subnet will have 248 in the 3rd octet.
D. The first 21 bits make the host portion of the address.
E. This subnet mask allows for 16 total subnets to be created.
F. The subnetwork numbers will be in multiples of 8.
第10题
A. It is a list of remote database links stored in the XML file that are available to the users of the database.
B.It is a list of users and network privileges stored in the XML file according to which a group of users can connect to one or more hosts.
C. It is a list of users and network privileges stored in the data dictionary according to which a group of users can connect to one or more hosts.
D. It is the list of the host names or the IP addresses stored in the data dictionary that can connect to your database through PL/SQL network utility packages such as UTL_TCP.


为了保护您的账号安全,请在“上学吧”公众号进行验证,点击“官网服务”-“账号验证”后输入验证码“”完成验证,验证成功后方可继续查看答案!

 微信搜一搜
微信搜一搜
 上学吧
上学吧



 微信搜一搜
微信搜一搜
 上学吧
上学吧