 题目内容
(请给出正确答案)
题目内容
(请给出正确答案)
The ________ who carried out the operation said that it had been a success.
A.surgeon
B.writer
C.youngster
D.conductor
 如搜索结果不匹配,请 联系老师 获取答案
如搜索结果不匹配,请 联系老师 获取答案
 题目内容
(请给出正确答案)
题目内容
(请给出正确答案)
A.surgeon
B.writer
C.youngster
D.conductor
 如搜索结果不匹配,请 联系老师 获取答案
如搜索结果不匹配,请 联系老师 获取答案
 更多“The ________ who carried out t…”相关的问题
更多“The ________ who carried out t…”相关的问题
第2题
A.Available dunnage,and chocking
B.Crushability,and inherent vice
C.Sweat,and weight
D.Weight,and refrigeration
第3题
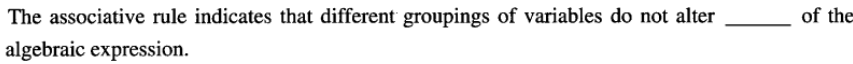
A、the order
B、the operational order
C、the validity
D、the form
第4题
M: Much better. The operation was a success and the doctor says she'll recover in no time and she'll probably come home at the weekend.
Q: What are the speakers doing?
(17)
A.Feeling better now.
B.Staying in a hospital.
C.Talking about the man's mother.
D.Doing an operation on a patient
第5题
A.The technical manager.
B.The sales manager.
C.The laboratory manager.
D.The operation manager.
第6题
It's easy for computer crimes to go undetected if no one cheeks up Mint the computer is doing. But even if' the crime is detected, the criminal may walk away not only unpunished but with a glowing recommendation from his former employers.
Of course, we have no statistics on crimes that go undetected. But it's disturbing to note how many of the crimes we do know about were de tected by accident, not by systematic inspections or other security procedures. The computer criminals who have been caught may have, been the victims of uncommonly bad hick.
For example, a certain keypunch operator complained of having to stay overtime to punch extra cards. Investigation revealed that the extra cards she was being asked to punch were for dishonest transactions. In another ease, dissatisfied employees of the thief tipped off the company that was being robbed.
Unlike ether lawbreakers, who must leave the country, commit suicide, or go to jail, computer criminals sometimes escape punishment, demanding not only that they not lee charged but that they be given good recommendations and perhaps other benefits. All too often, their demands have been met.
Why? Because company executives are afraid of the bad publicity that would result if the public found out that their computer had been misused. They hesitate at the thought of a criminal boasting in open court of how he juggled the most confidential records right under the roses of the company's executives, accountants, and security staff. And so another computer criminal departs with just the recommendations he needs to con tinue his crimes elsewhere.
It can be concluded from the passage that______.
A.it is still impossible to detect computer crimes today
B.1 computer crimes are the most serious problem in the operation of financial institutions
C.computer criminals can escape punishment because they can't be detected
D.people commit computer crimes at the request of their company
第7题
第8题
It's easy for computer crimes to go undetected if no one checks up on what the computer is doing. But even if the crime is detected, the criminal may walk away not only unpunished but with a glowing recommendation from his former employers.
Of course, we have no statistics on crimes that go undetected. But it's disturbing to note how many of the crimes we do know about were detected hy accident, not by systematic inspections or other security procedures. The computer criminals who have been caught may be the victims of uncommonly bad luck.
For example, a certain keypunch (打卡机) operator complained of having to stay overtime to punch extra cards. Investigation revealed that the extra cards she was being asked to punch were for dishonest transactions. In another case, dissatisfied employees of the thief tipped off (给…通风报信) the company that was being robbed.
Unlike other lawbreakers, who must leave the country, commit suicide, or go to jail, computer criminals sometimes escape punishment, demanding not only those they not be charged but those they be given good recommendations and perhaps other benefits. All too often, their demands have been met.
Why? Because company executives are afraid of the bad publicity that would result if the public found out that their computer had been misused. They hesitate at the thought of a criminal boasting in open of how he juggled (巧妙地应付) the most confidential records right under the noses of the company's executives, accountants, and security staff. And so another computer criminal departs with just the recommendations he needs to continue his crimes elsewhere.
What can we infer from paragraph 1?
A.The criminal could benefit from committing a computer crime.
B.Computer crimes are the most serious problem in nowadays society.
C.Criminals of computer crimes must be highly educated.
D.Anyone who commits computer crimes will be .punished immediately.
第9题
A.primarily manipulated by blood vessels
B.in constant need of training and practicing
C.much less complicated and coordinated
D.genetically programmed to work on its own


为了保护您的账号安全,请在“上学吧”公众号进行验证,点击“官网服务”-“账号验证”后输入验证码“”完成验证,验证成功后方可继续查看答案!

 微信搜一搜
微信搜一搜
 上学吧
上学吧



 微信搜一搜
微信搜一搜
 上学吧
上学吧